
Yesterday, Github was hit by the largest DDoS attack in history. “The attack originated from over a thousand different autonomous systems across tens of thousands of unique endpoints. It was an amplification attack using the memcached-based approach […] that peaked at 1.35Tbps via 126.9 million packets per second.”
This volumetric DDoS attack was unique in achieving its massive amount of power by relying on UDP-based memcached traffic. Memcached is free and open-source software that speeds up database-driven websites by caching data in RAM and reducing strain on disks or databases.
Hackers were able to exploit UDP’s vulnerability to spoofing by sending a small byte by flooding valid requests to an exposed Memcached server. This attack has a 10,000:1 amplification ratio, so on average, every byte an attacker sent to the exposed Memcached server, the server would then send 10 KB to the actual victim. Here is a diagram of what happened, courtesy of Cloudflare.
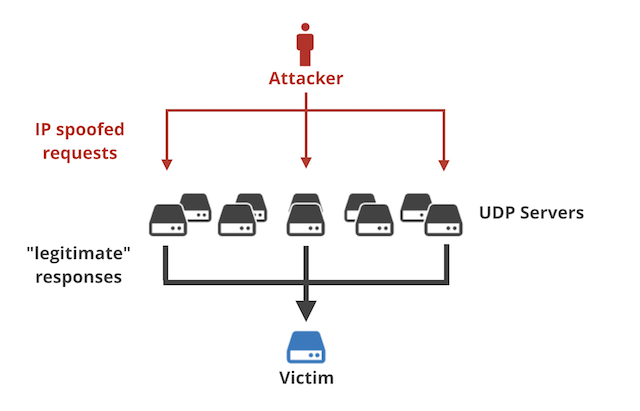
HostDime saw evidence that servers on our network could be directly affected. We have decided to block all packets with a UDP destination port of 11211 from entering our networks.
If you’re running Memcache within your server(s), our Network Administrators recommend you disable remote access if not needed and firewall off the service so only known authorized systems may access it. If you must use Memcache across facilities, you must use TCP or a site-to-site VPN to avoid putting the UDP service on the open Internet. Memcached over TCP isn’t vulnerable to this and traffic remains unblocked. Additionally, Memcached is now disabling UDP connectivity by default, so new installs shouldn’t be affected by this block.
For any questions you may have, don’t hesitate to comment below or open a support chat.

Thanks for the Precautions…