
KRACK WPA2 Vulnerability
This has been a busy week for vendors, attackers, and a public looking for security and protection. Early on October 16, Mathy Vanhoef, a researcher from the University of Leuven, discovered an extremely serious weakness in Wi-Fi Protected Access II (WPA2). This protocol secures ALL Wi-Fi networks, therefore putting millions of routers and Internet of Things devices at risk.
The exploit is called KRACK, or Key Reinstallation Attacks, and it is extensively documented here by Vanhoef, who explains:
An attacker within range of a victim can exploit these weaknesses using key reinstallation attacks (KRACKs). Concretely, attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted. This can be abused to steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and so on. The attack works against all modern protected Wi-Fi networks. Depending on the network configuration, it is also possible to inject and manipulate data. For example, an attacker might be able to inject ransomware or other malware into websites.
That’s right, your e-mail addresses and passwords aren’t the only thing at risk. Any data the victim transmits can be decrypted in this Man in the Middle attack.
KRACK is especially dangerous toward devices running Android, Linux, and OpenBSD, though macOS, Windows, Linksys, and others can be affected as well. Linux and Android 6.0 or higher get it the worst because attackers can force network decryption in seconds.
Vanhoef demoed the attack against a device running Google’s Android operating system, which shockingly reinstalls an all-zero encryption key thanks to the WPA2 exploit:
OK, so now what do we do now that our Wi-Fi device is vulnerable? Changing the password of your Wi-Fi network does not prevent the attack. Thankfully, many vendors have already released patches. Head over to the CERT website for their list. Users are urged to implement the new install update immediately.
RSA Encryption Key Vulnerability
As if this isn’t troublesome enough, right on the heels of this news comes an all new vulnerability affecting RSA encryption keys.
Hardware chips manufactured by Infineon used by PCs to generate RSA encryption keys have a vulnerability that could expose stored passwords, encrypted disks, documents, and more. Some devices that are affected include HP, Lenovo, Google Chromebooks, routers and many more. Check the official CERT site again to see if your PC was affected.
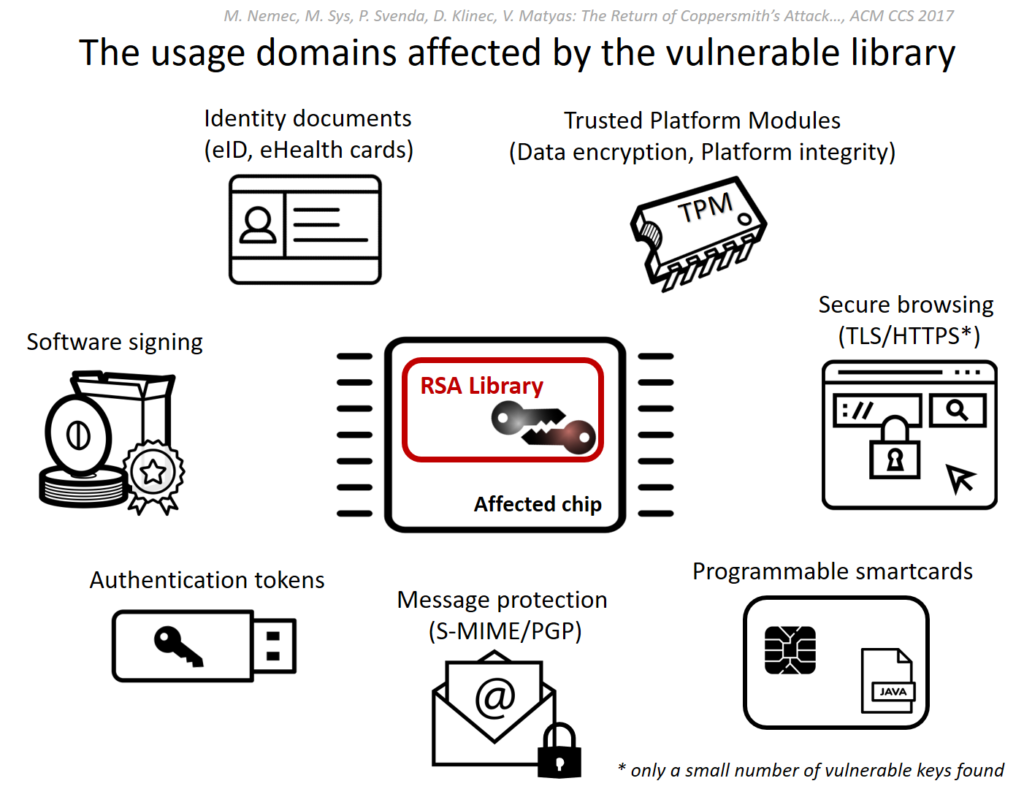
A remote attacker uses the target’s public key to generate an RSA private key with some time and computing power. Here’s an example based on an Intel E5-2650 v3@3GHz Q2/2014:
- 512 bit RSA keys – 2 CPU hours (the cost of $0.06)
- 1024 bit RSA keys – 97 CPU days (the cost of $40-$80)
- 2048 bit RSA keys – 140.8 CPU years, (the cost of $20,000 – $40,000)
The private key can be misused for actions like impersonation of a legitimate owner, decryption of sensitive messages, and fake signatures.
As we said, this has been an eventful week for vendors, who were fast to produce firmware updates. CERT even suggests replacing your device altogether if possible.
Stay safe out there, and continue to be informed with the constant stream of vulnerabilities that will inevitably follow.
[divider]
Jared Smith is HostDime’s SEO and Content Strategist.
